On 30 July 2023, several pools of Curve Finance, one of DeFi’s blue-chip protocols, was attacked by hackers, and approximately $70 million was stolen . The hack was done by exploiting a dormant zero-day vulnerability present in older versions of Vyper, which is a third-party EVM contract-oriented, pythonic programming language used by Curve and other decentralized protocols.
Curve Finance is a DeFi protocol that enables the decentralized exchange of stablecoins within Ethereum.
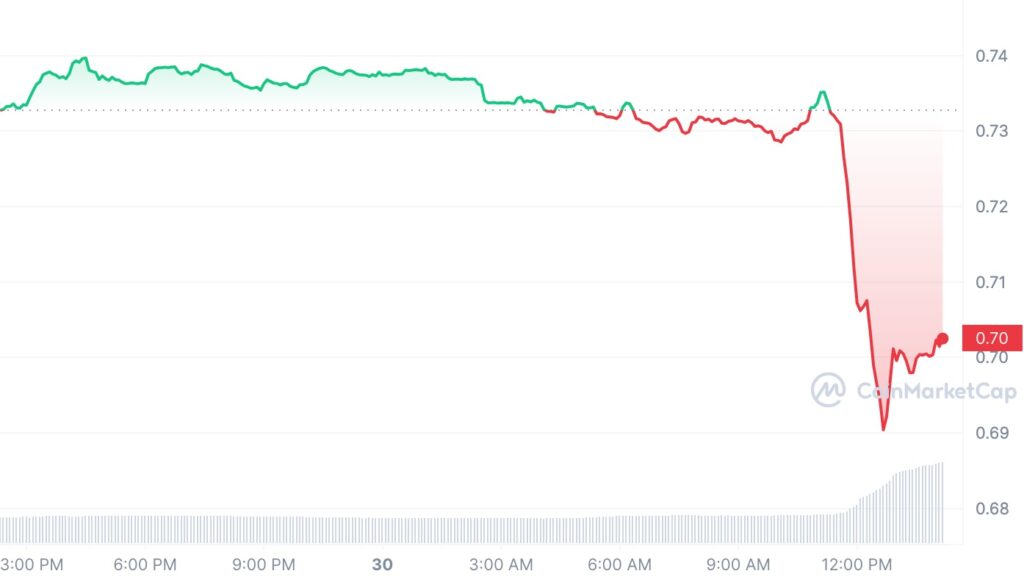
Over the next several days, Curve Finance was hit with by a cascading wave of panic selling and withdrawals. Within a short 48 hours period, Curve’s $3.2B TVL dropped by 50% to $1.6B, and the price of its CRV token fell by more than 30%, from $0.73 to $0.50. Losses from the exploit was estimated to be around $47 million.
Breakdown of the Events
This attack happened in two tranches. The initial attack hit the Alchemix (alETH), Pendle (pETH), CurveDAO (CRV) and Metronome (mSETH) pools on Curve and the second attack hit the CRV/ETH pool again a few hours after the first attack.
The second attack happened due to the CRV/ETH pool having broken balances as a result of the first exploit. This allowed the hacker to exchange a few CRV for most of the ETH left in the pool after syncing balances
Fortunately, a portion of the losses in the second attack was quickly contained due to the efforts of white hat hacker c0ffeebabe.eth, who returned roughly $5.4 million to Curve after her MEV bot successfully front-run one of the attacker’s transactions.
Analysis
According to initial investigation, some versions of the Vyper compiler do not correctly implement the reentrancy guard, which prevents multiple functions from being executed at the same time by locking a contract. Reentrancy attacks can potentially drain all funds from a contract.
Vyper is a contract-oriented, pythonic programming language that targets the Ethereum Virtual Machine (EVM). Vyper’s similarities to Python make the language one of the starting points for Python developers jumping into Web3.
According to Vyper, its 0.2.15, 0.2.16 and 0.3.0 versions are vulnerable to such malfunctioning reentrancy locks. Vyper has posted on their social media site X (formerly Twitter), reaching out to users of the older versions of Vyper to reach out to them.
BlockSec’s Warning
Interestingly, the vulnerability in the CRV/ETH pool was identified and tweeted by security firm BlockSec almost two hours before the attackers exploited the pool. This has led to several people, including Curve founder Michael Egorov, accusing the security firm of aiding attackers by “publicly broadcasting a live exploit.”
BlockSec has fought back against these accusations by stating that it had only meant to alert users of the new issue in order for them to take action and save funds. While the supposed intention behind BlockSec’s actions may have been good, whether it was really the best course of action remains debatable.

Closing Words
DeFi protocols have been targeted by multiple attacks over the past months. According to a report by Web3 portfolio app De.Fi, more than $204 million was swindled through DeFi hacks and scams in the second quarter of 2023 alone.
This is also not the first time a protocol within the Ethereum ecosystem has been targeted and attacked by hackers. Just a few days ago, its omnipool platform Conic Finance was exploited for $3.26 million in
ETH (Ether). Nearly the entire amount stolen sent to a new Ethereum address in just one transaction.
This article was written with information adapted from Coin Bureau and Coin Telegraph. We strongly encourage interested readers to check out this 2 media channels for quality updated cryptocurrency information.